Hackers Work 24/7. Does Your IT Provider?
Is Your Company Safe from Hackers? Let’s Secure Your Data!
OUR CYBERSECURITY SERVICES

Endpoint Detection and Response (EDR)

Multi-Factor Authentication (MFA)

Vulnerability Management (VM)

Advanced Email Security

Cybersecurity Awareness & Training


Penetration Testing (PenTest)

Application Zero Trust

Dark Web Monitoring

Compliance and Monitoring

Systems Information and Event Monitoring (SIEM)
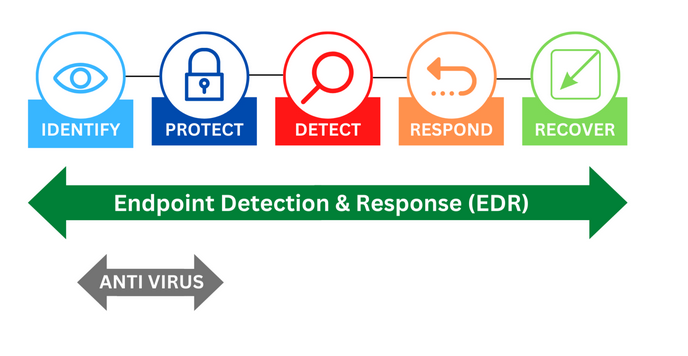
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is used to monitor, detect, investigate, and mitigate potential threats on system endpoints, including computers and servers. EDR is an integrated approach to endpoint protection. EDR can effectively stop incidents from happening.
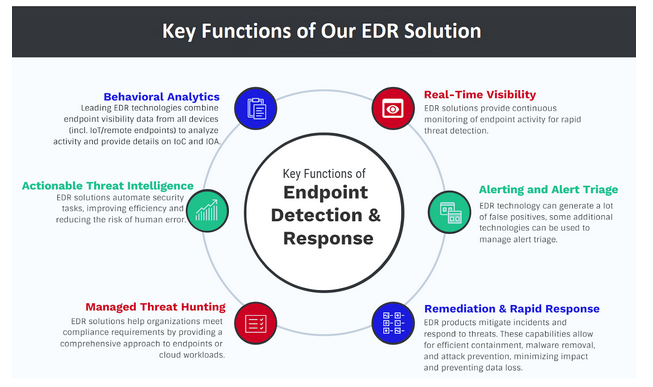
Why customers choose our Managed EDR Solution
- Real-Time Action to Block and Remediate Advanced Attacks Autonomously
- AI Powered Security to Prevent Threats, Reduce Risk and Protect Your Business
- Prevent Data Breaches
- Continuous Real-Time Visibility and Monitoring of Endpoints
- Autonomous AI Based Threat Detection and Response
- Accelerated Incident Response
- Increased Cost-Efficiency
- Greater Protection for Remote Work Force
- Centrally Managed
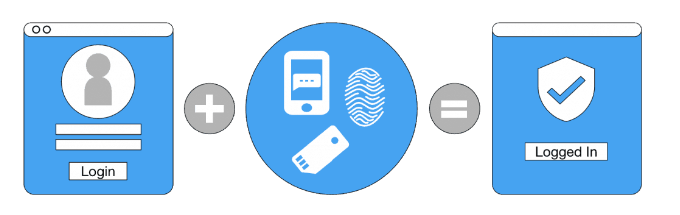
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) uses a combination of two or more separate authenticators to confirm a user’s identity during login, more than just a password. A properly implemented MFA solution can make your organization’s intellectual property much more secure. Digital security is critical in today’s world because both businesses and users store and access sensitive information. Users interact with applications, services, and data that are stored on their corporate servers as well as in the cloud using online accounts. A breach, or misuse, of this sensitive information could have serious real-world consequences, such as financial theft, business disruption, and loss of privacy. While passwords protect digital assets, they are simply not enough. Expert cybercriminals try to actively find passwords through various means, such as phishing, deception, malware, etc. Multi-Factor Authentication acts as an additional layer of security to prevent unauthorized users from accessing these accounts, even when the password has been stolen. Businesses use Multi-Factor Authentication to validate user identities and provide quick and convenient access to authorized users. Adding Multi-Factor Authentication is the #1 action most enterprises can do to prevent cybersecurity incidents from occurring
Why customers choose our Managed MFA Solution
- Stronger Authentication
- Secure Against Identity Theft Via Stolen Passwords
- Protect your Business
- Protect Against Weak Employee Passwords
- Secure Cloud Applications
- Meet Compliance Requirements
- Increased Security
- Secure Enterprise Mobility Access (VPN)
- Secure Lost or Stolen Device
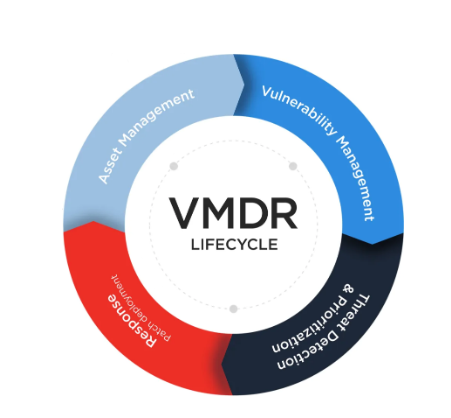
Vulnerability Management Detection and Response (VMDR)
Vulnerability Management Detection and Response (VMDR) is a solution that scans enterprise networks to identify weaknesses that intruders may exploit. It detects vulnerabilities on all network assets, including servers, workstations, switches, firewalls, routers, etc. Vulnerability scanning gives you immediate visibility into your IT system’s vulnerability and compliance posture. Since most breaches occur by exploiting vulnerabilities, it is important to discover, access, prioritize, and patch critical vulnerabilities and misconfigurations in real time. The threat landscape is changing, new cyber risks emerge daily. Are you overwhelmed with vulnerabilities? Do you have an accurate picture of the assets on your network and where you are vulnerable?
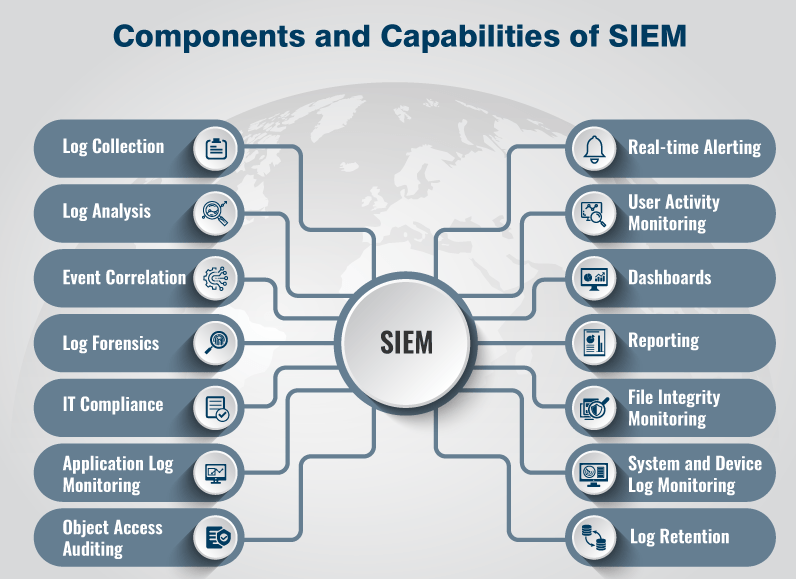
System Information and Event Monitoring (SIEM)
System Information and Event Monitoring (SIEM) is a component of a comprehensive cybersecurity solution that collects, converges, and analyzes logs and event information from different components of IT systems, such as servers, firewalls, switches, routers, etc. At its core, SIEM assists with managing security by filtering massive amounts of ingested security data and prioritizing the security alerts the software generates.
Schedule an Appointment with IT Network Solutions Today!
Let’s explore how we can help with your IT support and consulting needs. Complete the form on the right, and we’ll reach out to you to learn more about your organization’s IT requirements and discuss how we can assist.
What Our Clients Have To Say
IT Expertise for Current and Future Challenges
Our experience with ITNS has been transformative, highlighting their expertise in IT management and customer service. Their approach not only solves immediate IT challenges but also strategically positions our company for future technological advancements. ITNS is more than just an IT firm; they are a vital partner in our ongoing business success.
Uptime and Peace of Mind are Top Priorities
IT Network Solutions has completely removed the stress of IT from our business. As a CPA firm, system uptime during tax season is non-negotiable, and ITNS gets that. Their rapid response time and proactive support give me total confidence that we’re covered, even during our busiest periods. On top of that, their team is friendly, easy to work with, and their system is incredibly user-friendly. If uptime and peace of mind matter to your business, I can’t recommend IT Network Solutions highly enough.
Over a Decade of Unmatched IT Support and Professionalism
IT Network Solutions has been a reliable and professional partner for more than a decade, they have always exceeded expectations. Their customer support is responsive and available, which we really appreciate. We are extremely satisfied and would highly recommend their services.
Reliable IT Support with Exceptional Customer Service
We are grateful to IT Network Solutions for their outstanding customer support. Whenever we encounter technical issues, their responsive and knowledgeable team is quick to resolve them. Their commitment to customer satisfaction is truly commendable
A 19-Year Partnership Built on Trust and Expertise
I have known and worked with IT Network Solutions for 19 years. Their level of expertise has not only helped the organization streamline and run extremely efficient networks but has, at the same time, raised my level of knowledge and understanding way beyond what I could have achieved by other means. They have gone way above and beyond for me on more occasions than I care to admit and helped me out of seemingly impossible situations – sometimes in the middle of the night -all with the caring and patience that one cannot possibly assign a price tag.


